In this series of blogs, we are reviewing the best practices in hardening your Microsoft 365 tenant against malicious attacks. Many attacks can be block by making zero-costs changes to your tenant. Organizations need to enable people to access resources securely without impacting their productivity. Having multiple usernames and passwords for different apps and services is a security risk, especially when you don’t control access to the app (such as with third-party SaaS apps). Azure AD Application Proxy enables organizations to implement secure remote access to on-premises applications so remote users can access them in the same manner they access cloud applications.
Microsoft recommends four requirements for implementing strong identity for a Zero Trust security model:
- Multi-factor Authentication (MFA) – Read more
- Policy-based access – Read more
- Identity Protection – Read more
- Secure access to SaaS and on-premises apps
In this blog, we are going to discuss the fourth security recommendation: Securing access to SaaS and on-premises apps with Azure AD Application Proxy.
To Start, let’s review Zero Trust Model.
What is Zero Trust?
Instead of believing everything inside the organization’s firewall is safe, the Zero Trust model assumes breach and a “never trust, always verify” access approach. Every request, regardless of whether it originated internally or externally, is strongly authenticated, authorized, and inspected for anomalies.
Now, let’s discuss securing accessing to SaaS and on-premises apps and why it is a Microsoft Recommendation.
Organizations need to enable people to access resources securely without impacting their productivity. Having multiple usernames and passwords for different apps and services is a security risk, especially when you don’t control access to the app (such as with third-party SaaS apps).
By connecting the sign-in experience for all your apps (on-premises, cloud, and third-party SaaS apps) from any device and managing user directories together, you gain better control and visibility, and simplify the experience for users. You can reduce the risk posed by multiple credentials for outside apps if they are connected to a single sign-on process. In addition to Microsoft services (Office 365, Azure, Dynamics), Azure AD has an app gallery of thousands of pre-integrated third-party SaaS apps to simplify single sign-on for your users. Plus, you can add your own custom applications easily in the portal.
What is Azure AD Application Proxy?
Azure AD Application Proxy enables organizations to implement secure remote access to on-premises applications so remote users can access them in the same manner they access cloud applications. It does this by externalizing on-premises apps over HTTPS. By signing in to Azure AD once, users can access both cloud apps and on-premises applications via an external URL or an internal portal.
Azure AD Application Proxy also allows on-premises applications to leverage Azure’s security analytics and authorization controls. This makes it easier for organizations to implement the same conditional access and MFA policies across cloud apps and internally hosted applications. Because Azure AD Application Proxy is hosted in the cloud, no additional software components or network changes are required to enable remote access to on-premises applications.
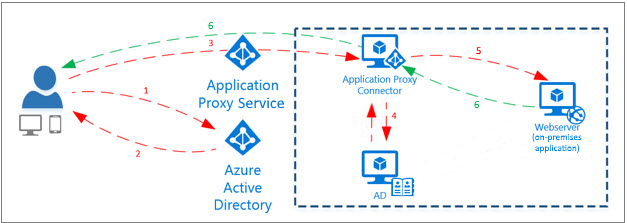
Application Proxy also eliminates the need for virtual private networks (VPNs) by serving as a reverse proxy for remote access to on-premises apps. It includes a cloud-based Application Proxy service and a lightweight Application Proxy Connector that runs on a Windows server hosted on-premises.
When a remote user signs into the app with Azure AD, a sign-in token is sent from Azure AD to the user’s device, which the Application Proxy uses to authenticate the user.
The token is sent to the connector, which performs additional authentication if needed and connects the user to the requested app (if SSO is enabled). The Application Proxy Connector manages communications between the Application Proxy service and the on-premises application. The Connector only uses outbound connections to communicate with the Proxy Server, so inbound ports need not be opened in the firewall.
Azure AD Application Proxy works with applications hosted behind a Remote Desktop Gateway, with web apps that use Integrated Windows Authentication and APIs that organizations want to expose externally.
As an alternative to Application Proxy, Microsoft also has partnerships with security providers including F5, Zscaler, Citrix, and Akamai. These partnerships are designed to simplify secure access to legacy applications that use protocols such as header based and Kerberos authentication, using Azure AD.
How it works
Conclusion
Zero Trust is a journey, not a destination. And the journey is unique to every organization because of differences in enterprise architecture, available resources, and priorities. Regardless of your unique needs, moving from an access model based on implicit trust to a Zero Trust model based on explicit verification requires careful planning and time.
Identities are a logical starting point for implementing a phased Zero Trust security model. Microsoft 365 E5, with its strong authentication, identity protection, and access control capabilities, provides a solid foundation for organizations to get started on their Zero Trust journey.