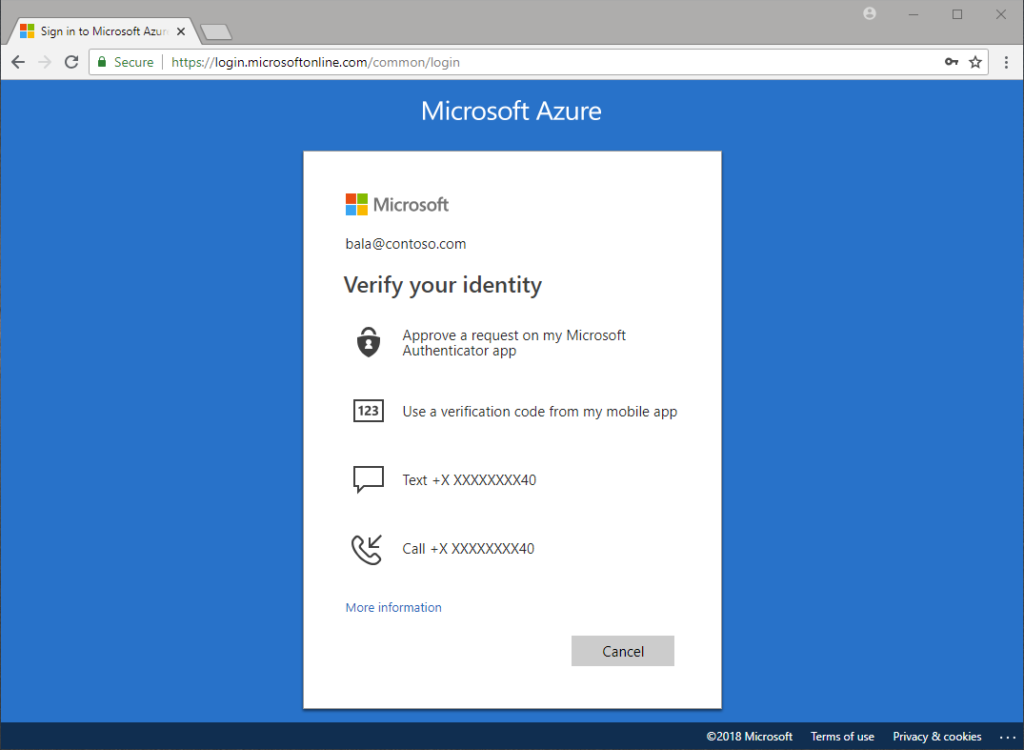
A recent survey of Microsoft Office 365 accounts found that over 75% have yet to implement MFA. From a cost of security perspective, this is the single most powerful deterrent to hackers available. Very few hacks of IT systems are capable of beating MFA when properly deployed. Also, the user impact of Microsoft’s Office 365 MFA is very light. We strongly recommend all IT administrators deploy first to the ADMIN staff and then to all users.
In this series of blogs we are reviewing the best practices in hardening your Microsoft Office 365 tenant against malicious attacks. Many attacks can be blocked by making zero-cost changes to your tenant.
Microsoft recommends four requirements for implementing strong identity for a Zero Trust security model. Today we will discuss Multi-factor Authentication (MFA). See the four requirements for strong identity below:
- Multi-factor Authentication (MFA)
- Policy-based access
- Identity Protection
- Secure access to SaaS and on-premises apps
To start, lets review the Zero Trust Model.
What is Zero Trust?
Instead of believing everything inside the organization’s firewall is safe, the Zero Trust model assumes breach and a “never trust, always verify” access approach. Every request, regardless of whether it originated internally or externally, is strongly authenticated, authorized, and inspected for anomalies.
Now, let’s discuss Multi-factor Authentication and why it is a Microsoft Recommendation.
What is Multi-factor Authentication (MFA)?
Multi-factor Authentication, also known as MFA, adds an additional layer of defense by requiring users to provide two or more forms of authentication to access an account. The forms of authentication can include something the user knows (such as a password), something they have (such as a phone or other trusted device), or something that makes up who they are (such as a fingerprint or other biometric).
Why should you have Multi-factor Authentication (MFA)?
Password-only authentication mechanisms are no longer sufficient to protect user accounts. Users from inside and outside the organization are using a variety of devices, including unmanaged personal smartphones and tablets.
In this environment, weak login credentials can provide attackers with easy entry to gain unchallenged access to your resources.
Most importantly, Azure MFA delivers strong authentication for securing access to critical data and applications. Users may be challenged for additional authentication based on contextual data about their login, geolocation, access request, system configuration details, and other signals.
The second-factor authentication methods that Azure Multi-factor Authentication MFA supports include the following:
- Microsoft Authenticator App – sends a push notification to smartphones that require users to verify access
- Windows Hello for Business – replaces your passwords with two-factor authentication on Windows 10 PCs with credentials tied to your device, as well as a PIN, fingerprint, or facial recognition
- SMS messages – can be sent to registered device, requiring users to enter a verification code to sign in to an app or service
- Automated voice calls – enable users to sign in by pressing the # key on their registered mobile device
- Security questions – let users authenticate by answering a set of predefined questions
Do I have to use MFA each time I sign in?
No. You can set Multi-factor Authentication value between 1 – 365 days.
Review this article from Microsoft on limitations.
In part two, we will discuss Policy-based Access.
Contact Enclyne for support in enabling Multi-factor Authentication.